Spring is Back! FormulaShare Spring '25 Release
MAJOR RELEASE
Another year flies by... birds are blooming and flowers singing, and it's time for our annual major release!

Another year flies by... birds are blooming and flowers singing, and it's time for our annual major release!
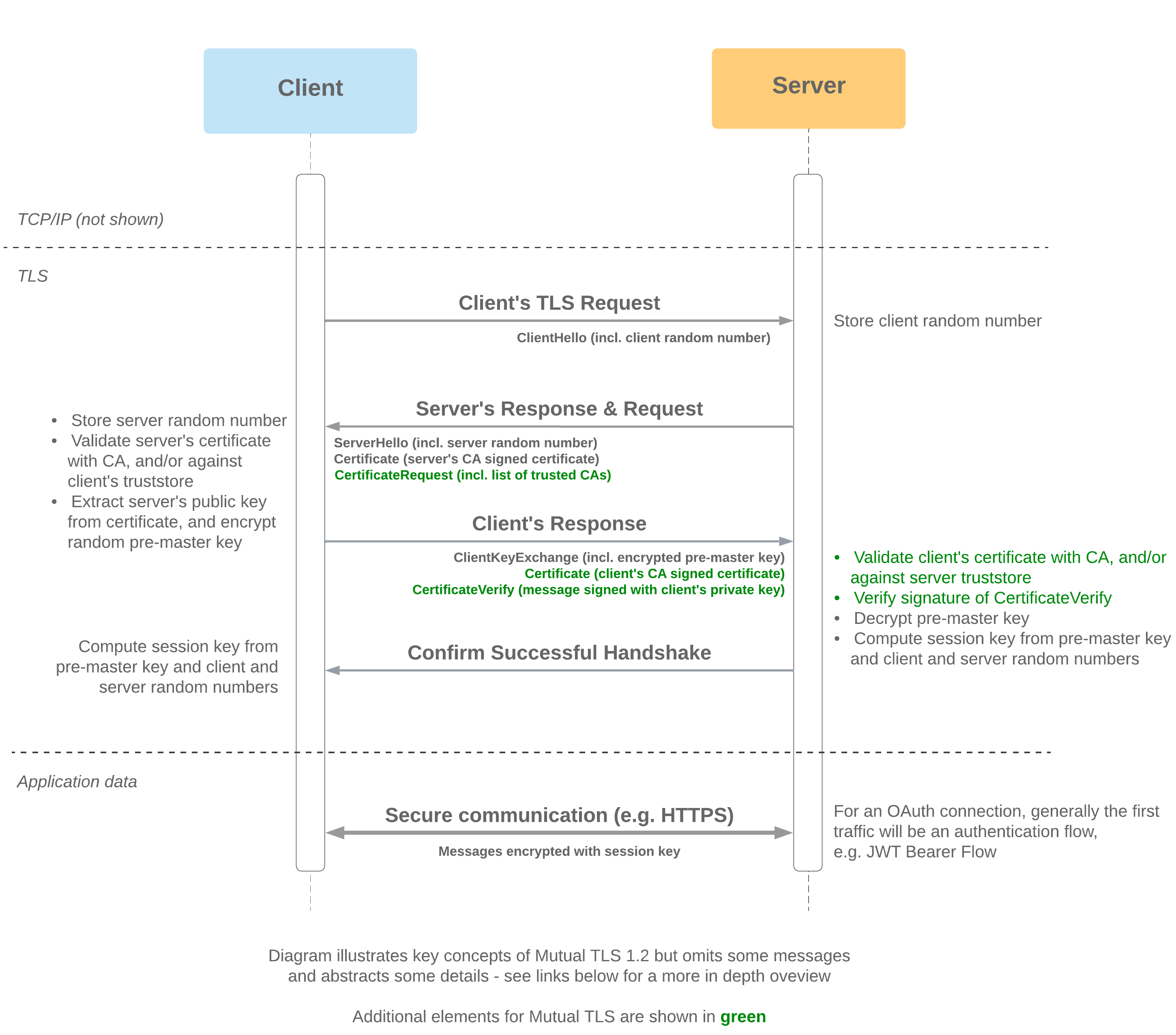
Each of the flow articles and identity pages now include versions of a diagram showing how each of the flows fit into the landscape of technologies used in SSO and OAuth 2.0.
These are based on a diagram from a set created by Jesse Lingo, showing how the flows can be grouped by technologies involved and the context in which they're used:
We've been hard at work adding FormulaShare features, improvements and fixes. We're really excited about the changes which offer more flexibility and help to move away from code altogether!
The Spring release includes new enhancements, but has no expected impact to your existing functionality. You'll be pleased to know no changes are needed unless you'd like to adopt some of the exciting new features.
FormulaShare is nearly five years old. From April 2023 the project is moving to the next level of maturity, with free and subscription-based options soon becoming available on the AppExchange.
I wanted to take a few moments to explain why...
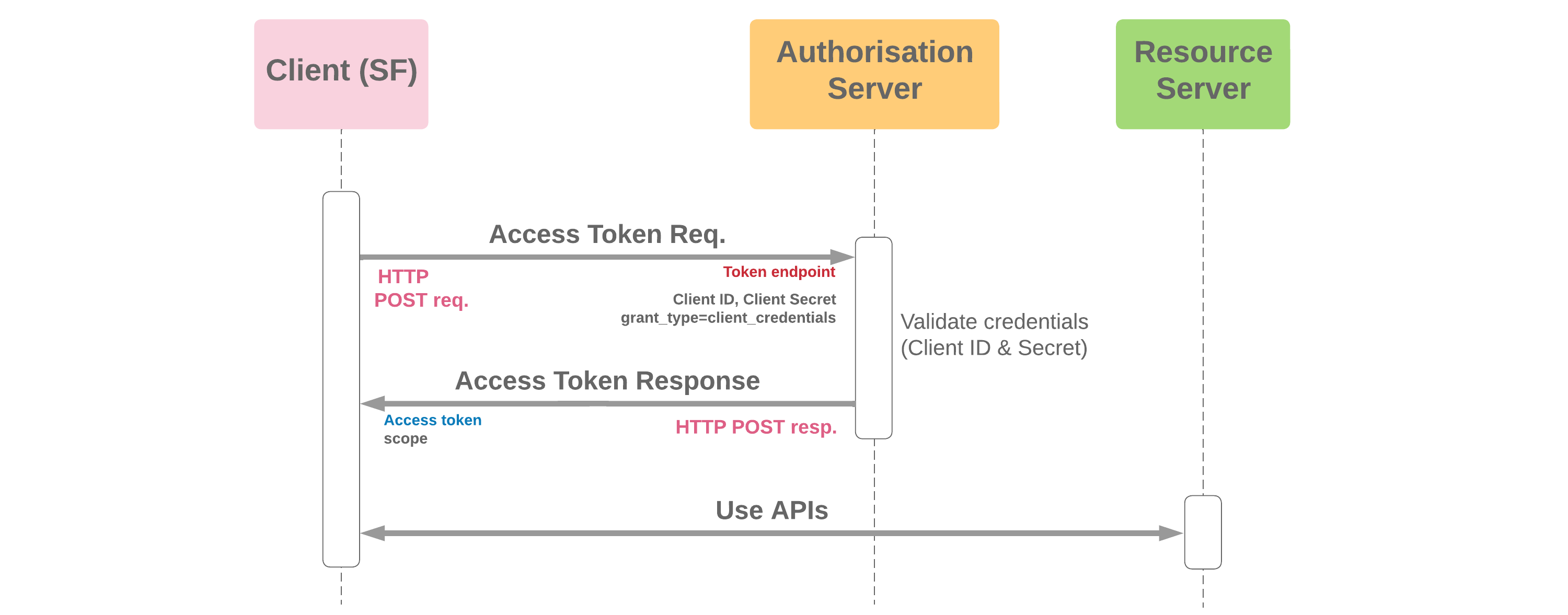
When Salesforce acts as the Client (e.g. Apex callout)
When Salesforce acts as the Server (e.g. Apex REST service)
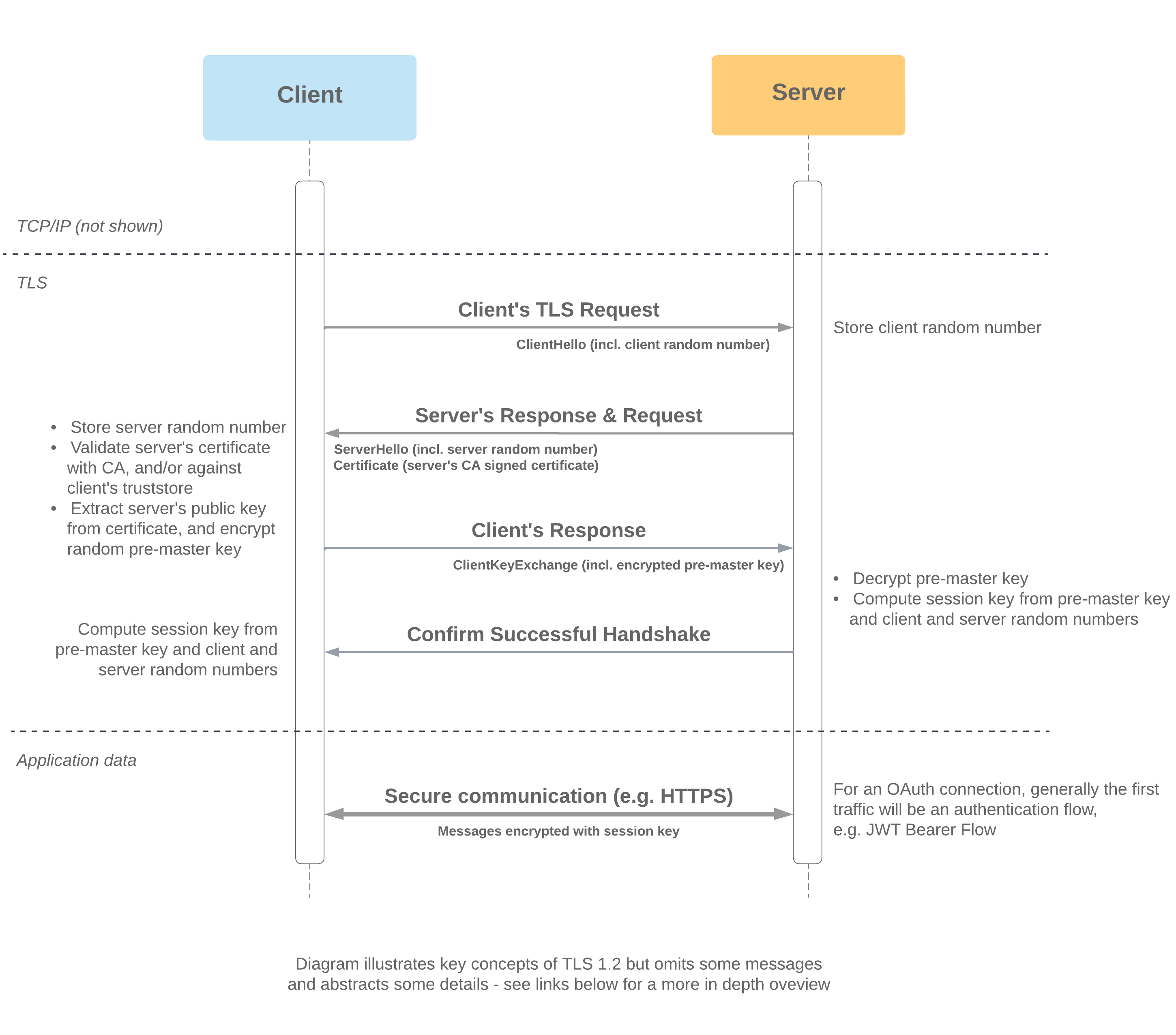
When Salesforce acts as the Client (e.g. Apex callout)
When Salesforce acts as the Server (e.g. Apex REST service)
Experimenting with your own org is the best way to really get to know these flows and understand how they're configured in practice.
Trigger frameworks - not something we'd look to change too often. But let's say we're working on a brand new org, or looking for something to complement a change in strategy. Shall we copy-paste that framework which worked well for so long? Or find the one on Github with the most stars?
Let's first put cards on the table - traditional trigger frameworks don't play well with modern development practices in Salesforce.
The next major release is here! There are a few big enhancements coming in this version:
Cross-object sharing rules (Lite, Enterprise and Unlimited)
This is a big one! FormulaShare allows information from related objects to determine sharing, and we've boosted this ability in a big way.
It's now possible to share based on a field in an object connected through a series of lookups to the shared object.