Standard (One-Way) TLS
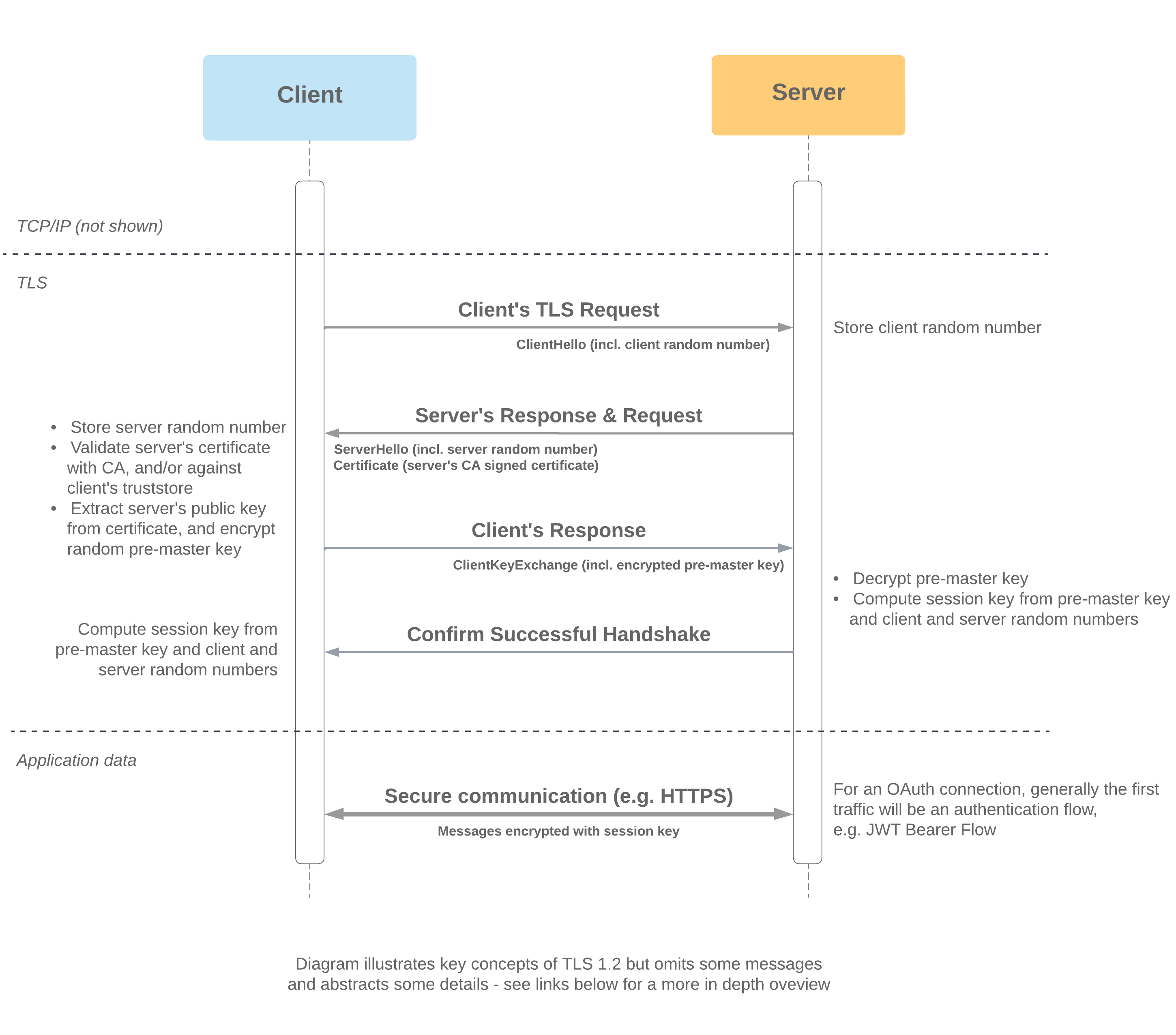
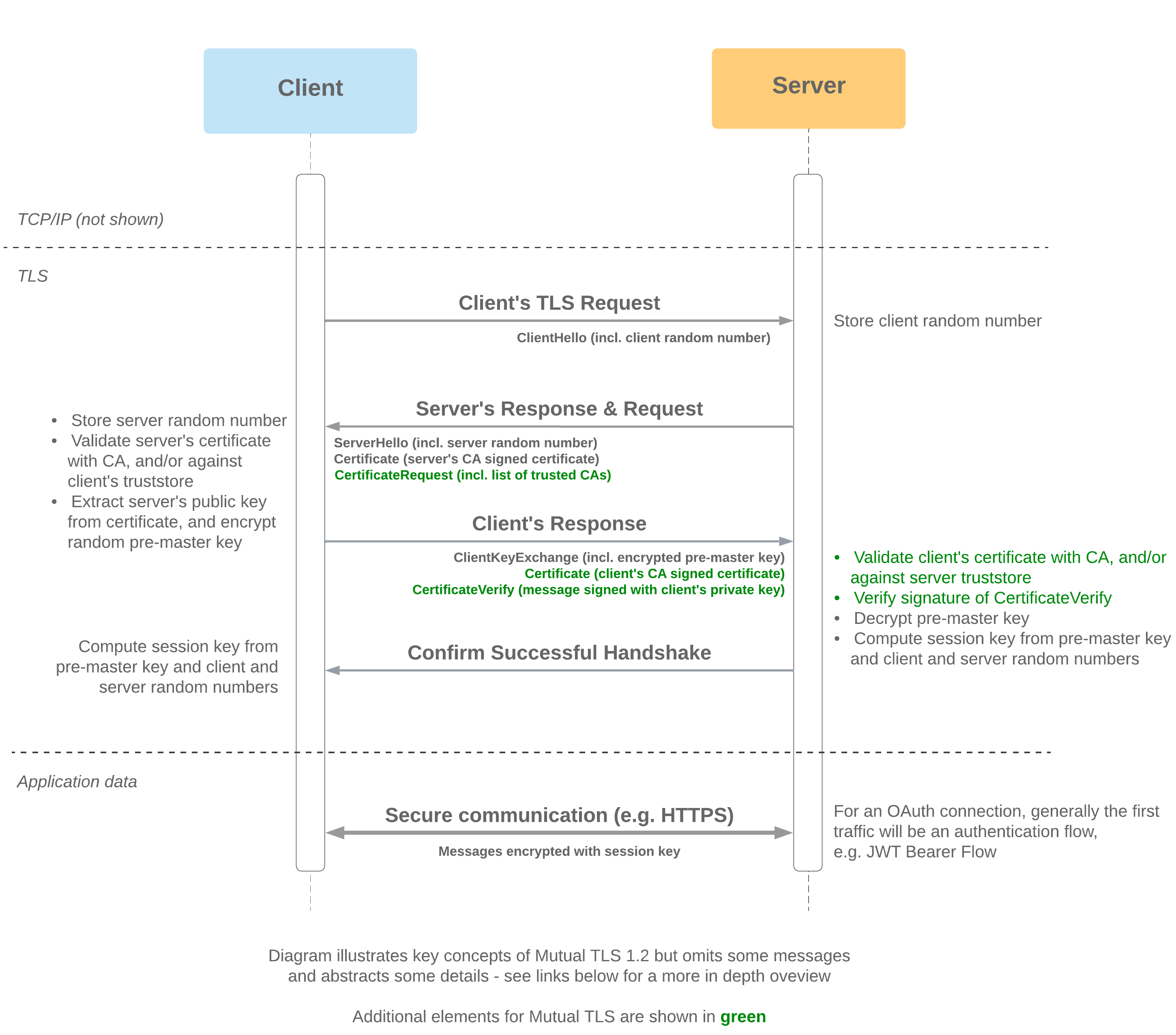
- TLS (Transport Layer Security) takes place at the network layer and precedes all HTTPS traffic, including user authentication
- The client may be a browser or a client application participating in server-server integration
- One-way TLS protects against impersonation of the server, as the server proves its identity to the client by demonstrating possession of its private key
- The goal is for the client and server to establish a secure connection by establishing cryptographic keys that will be used to protect data in transfer
- The shared session key required for HTTPS is generated from the pre-master key, client and server random numbers - both client and server require all of these to generate matching keys
- Server identity is conferred by its ability to decrypt the pre-master secret to generate a session key matching the one generated by the client
When Salesforce acts as the Client (e.g. Apex callout)
- Salesforce will only trust a CA signed certificate from the server
When Salesforce acts as the Server (e.g. Apex REST service)
- Salesforce will present its CA-signed certificate (this certificate is managed by Salesforce and independent of the customer's org)
- A client can connect to the My Domain login URL via port 443