OAuth 2.0 Flows
Salesforce supports several flows from the OAuth 2.0 authorisation framework:
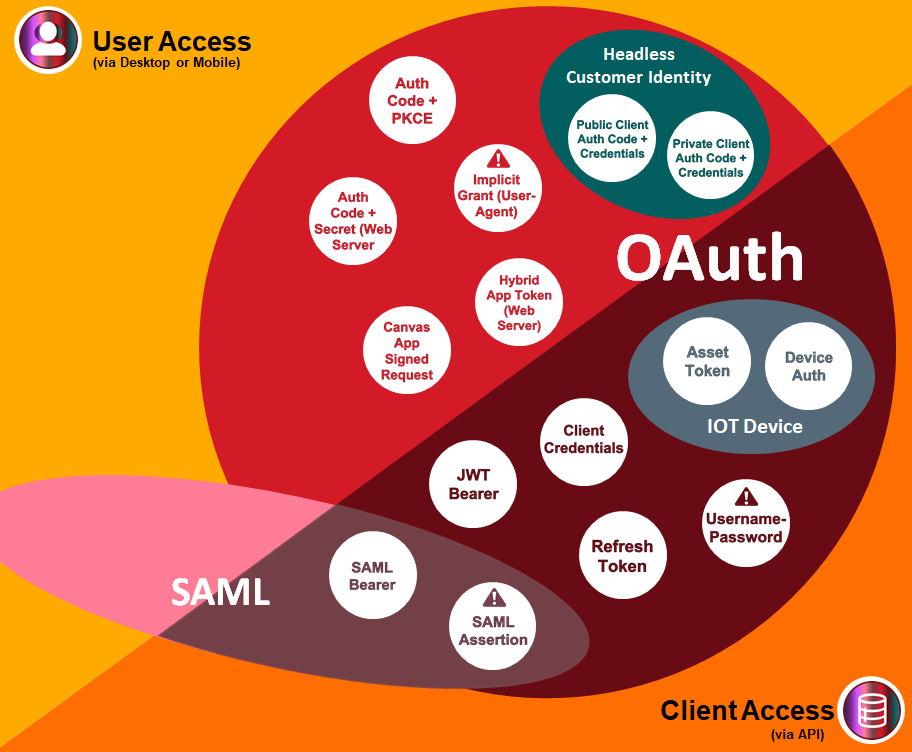
Each of these flows provide the means for a client (a browser, server or device) to acquire an access token, which can subsequently be used to make authenticated requests for protected resources from a resource server. The choice of which flow is most appropriate for a given context depends on the type and level of trust in the client application, the role of the end user in the process and the security assurances required.
The flows are grouped according to the type of client application which would typically be involved:
- Browser Access OAuth Flows - Includes flows which are most commonly used to authorise and provide resources to a browser client. During these flows, the user may be interacting directly to log in to the authorisation server and provide consent to share information. These are the OAuth flows in the "User Access" section of the diagram above.
- Server Access OAuth Flows - Covers flows which are most often used in server-to-server authentication which can be carried out without real time user interaction. These are the OAuth flows in the "Client Access" section of the diagram other than the IOT Device flows.
- Device Access OAuth Flows - Details the steps of flows which are designed to allow smart devices without a browser to interact with a Salesforce instance. These are the flows in the "IOT Device" segment of the diagram.
For flows where Salesforce can play the role of either the client or resource and authorisation server, the diagrams and notes describe characteristics of the flow in general terms. Considerations specific to implementations involving Salesforce are mentioned in the notes.
Flows which involve a user providing authentication and authorisation show these steps at a high level. A more detailed summary of the steps involved is outlined in OAuth 2.0 Login and Consent.
