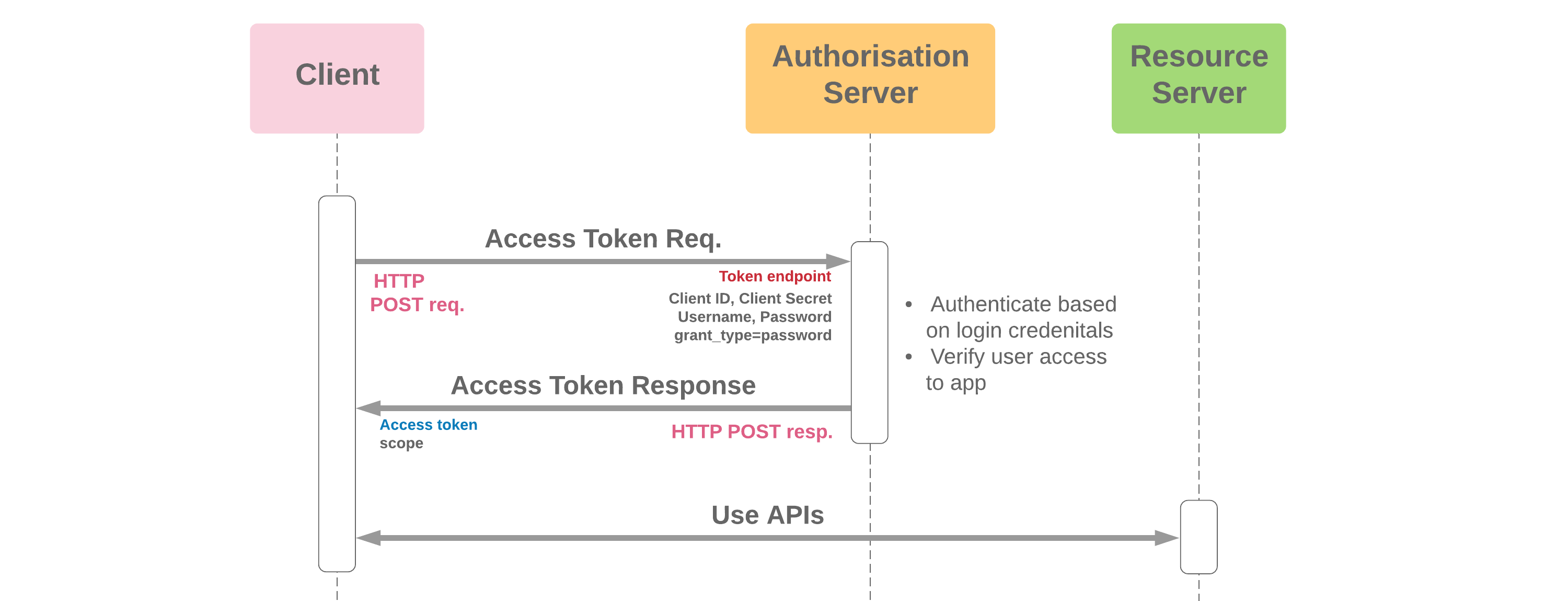
Server Access OAuth 2.0 Flows
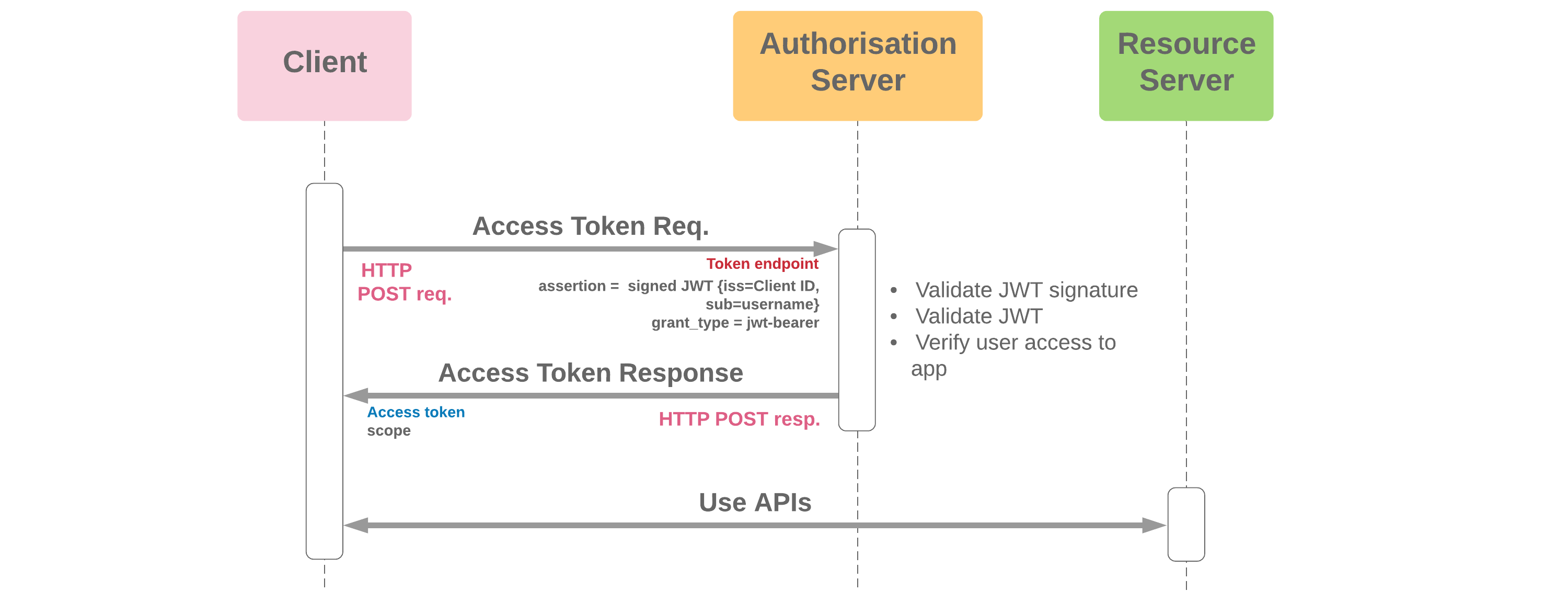
- JSON Web Token (JWT) is created and signed with private key of an X509 certificate by client app
- Authorisation server checks signature against public key of certificate to verify authenticity of request
- Allowed scopes are based on approval previously provided by the user through another OAuth flow
- Additional claims can be included in the JWT to communicate extra user or context info to the auth. server
- For Salesforce to act as the authorisation & resource server, a connected app is needed. This flow is used in Salesforce DX CLI authorisation
- Salesforce can also act as the client, and an option is offered in Named Credentials to make callouts from Salesforce to an external server application using this flow
- SAML assertion is created and signed with private key of an X509 certificate by client app
- Authorisation server checks signature against public key of certificate to verify authenticity of request
- Allowed scopes are based on approval previously provided by the user through another OAuth flow
- Additional claims can be included in the assertion to communicate extra user or context info to the auth. server
- For Salesforce to act as the authorisation & resource server, a connected app is needed
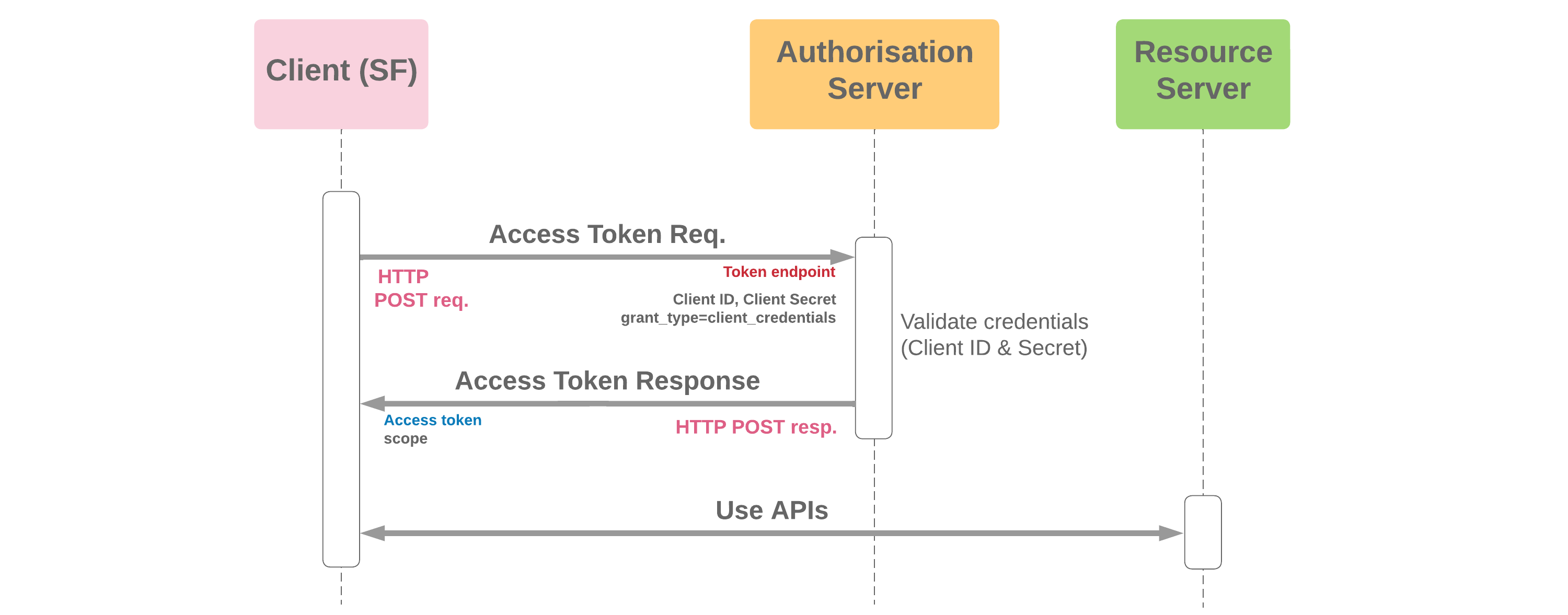
- The client credentials grant flow is used for server-to-server interaction, and allows clients to obtain an access token outside of the context of a user
- Since client authentication is used as the authorisation grant, no additional authorisation request is needed
- As with other server-server flows, a refresh token will not be supplied
- Salesforce can act as the client, and as of Winter '23, Salesforce also supports this flow while acting as the server. When Salesforce participates as the server, an execution user must be selected in the connected app which determines the running user and permissions for any integration activity
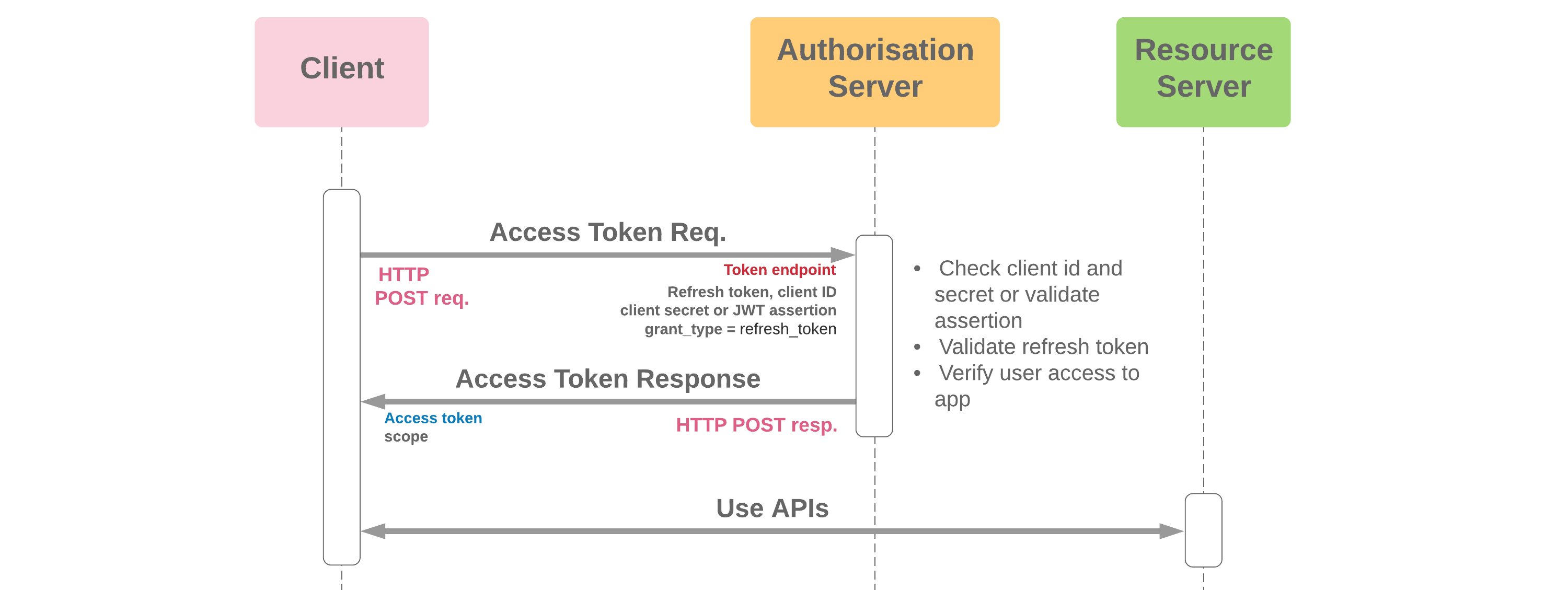
- Used to exchange a refresh token for an access token when required
- An app will need to invoke this flow each time an access token expires. Access token expiry can be identified by a status code 401 ("Unauthorized") or sometimes 403 ("Forbidden") error response from a resource server endpoint. If Salesforce is the resource server, this response will be 401 with error code "INVALID_SESSION_ID"