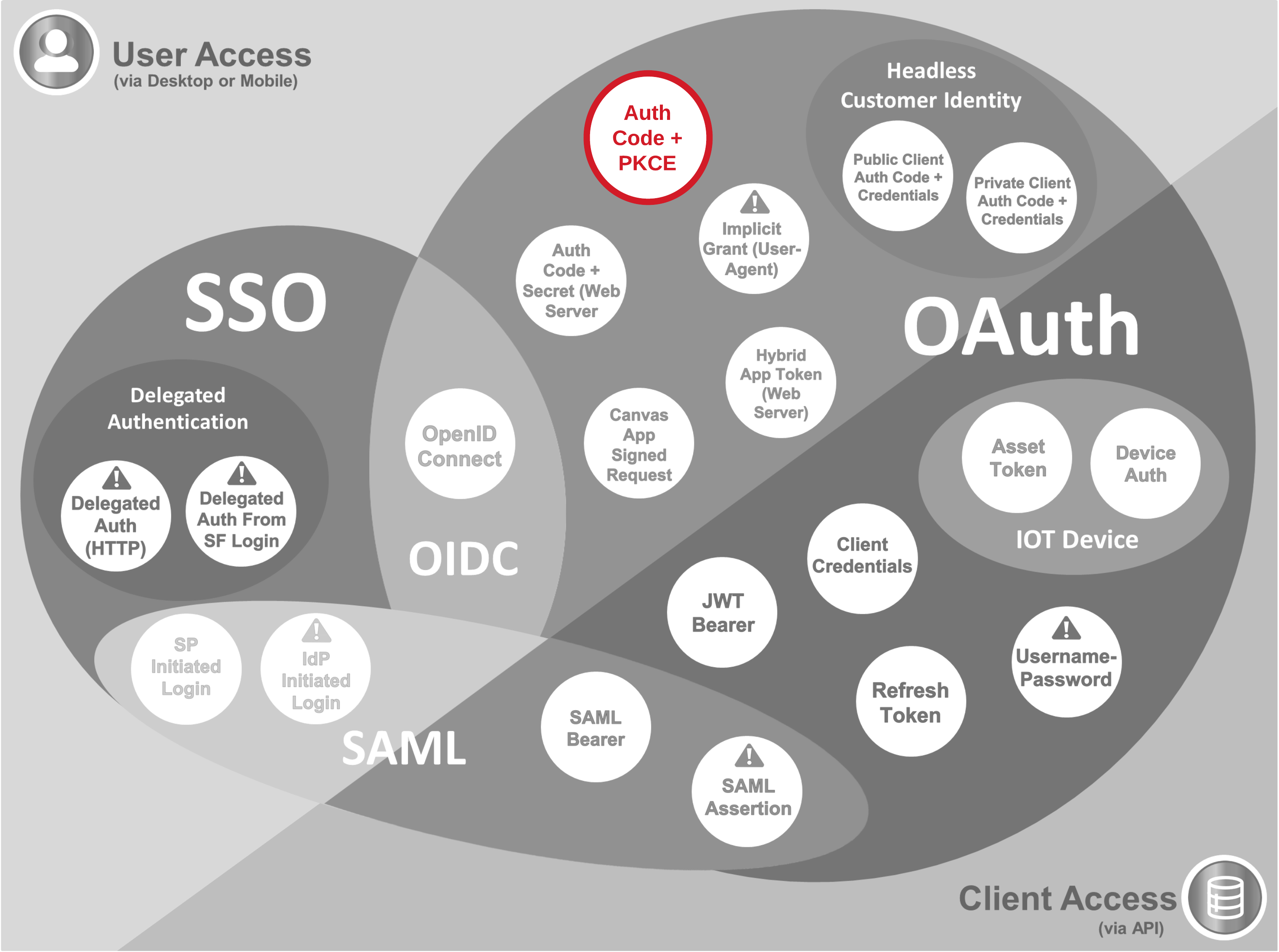
- Since 2017, Authorisation Code with PKCE (Proof Key for Code Exchange) has been recommended as the most secure flow for mobile and native apps by the Internet Engineering Task Force (IETF). Their white paper recommendation is linked below
- The major advantage this has over implicit grant (User-Agent) is that although there's no need for the client to protect credentials or a secret, tokens are returned through a secure channel (an out of band HTTPS call) rather than via the browser URL, which carries risk of a token being leaked through browser history or URL referrals
- PKCE refers to the use of "code verifier" and "code challenge", which provide an additional layer of security. Code verifier is a 128 byte base64url encoded random string generated by the app, and code challenge is the base64url encoded SHA256 hash of this string
- Native apps may make use of a custom URL scheme (e.g. MyApp://) or localhost (e.g. http://localhost/) to capture redirects - exposing authorisation codes issued for this flow carries low risk
- The authorisation server checks the application is making an authorised token request by comparing code challenge to the hash of code verifier. When these match, the authorisation server can be confident the entity making the token request is the same one which requested the authorisation code - the one-way nature of the hash function makes it difficult for an attacker to find a matching code verifier and so impersonate the authorised client even if code challenge and auth code are intercepted
- To configure Salesforce as an authorisation server allowing this flow, a connected app is needed with the option "Require Secret for Web Server Flow" disabled
Documentation