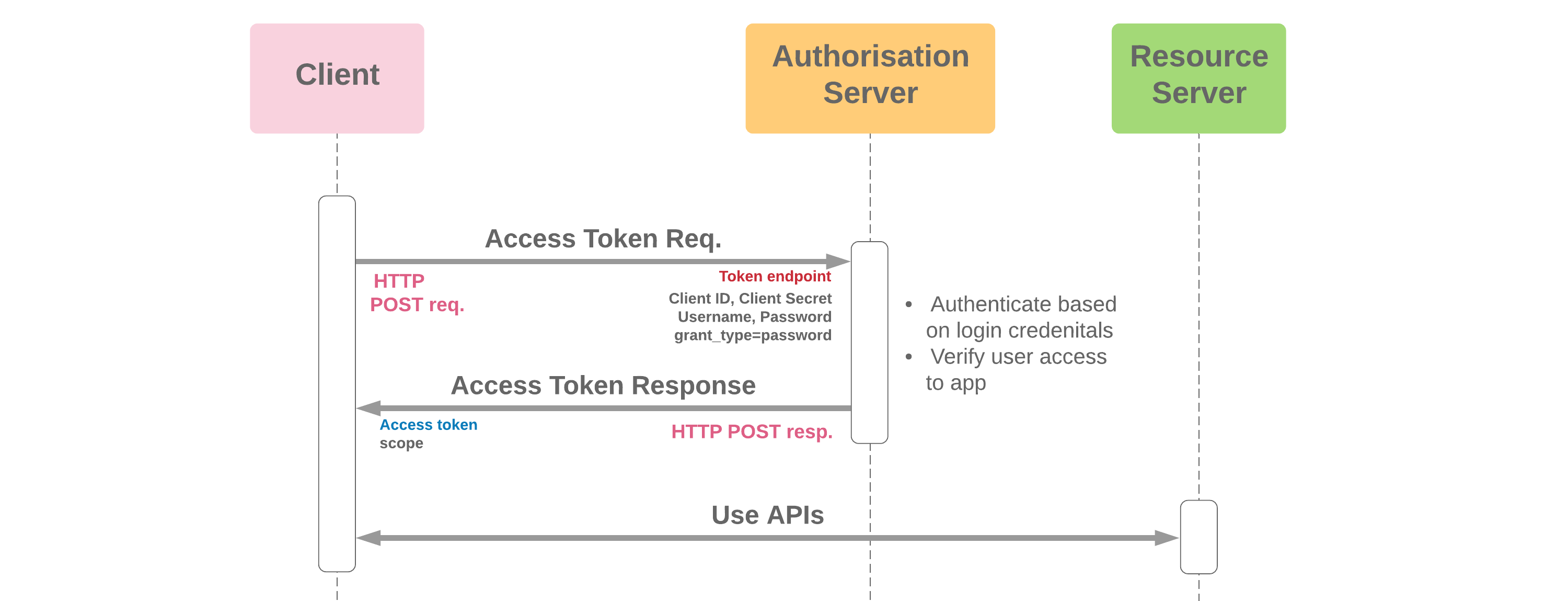
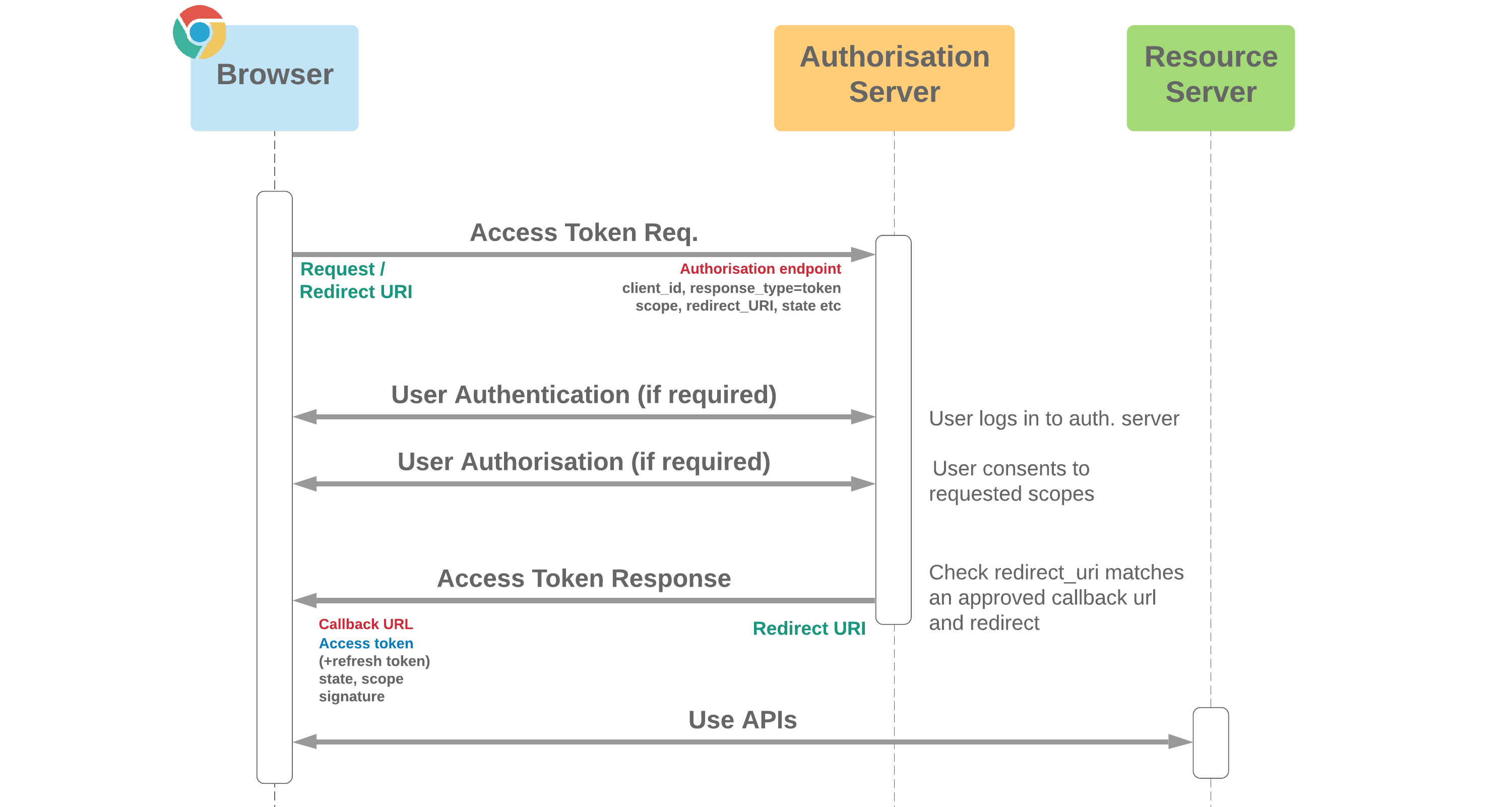
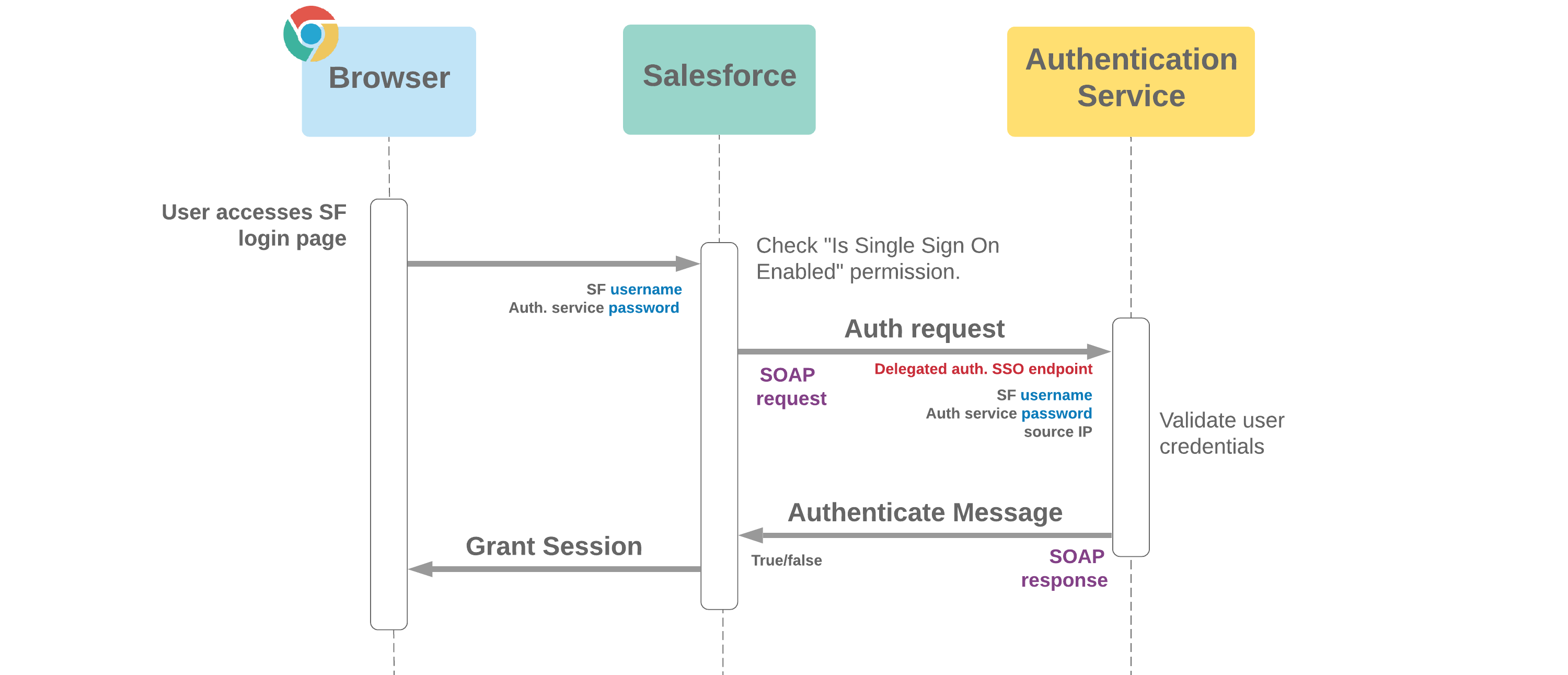
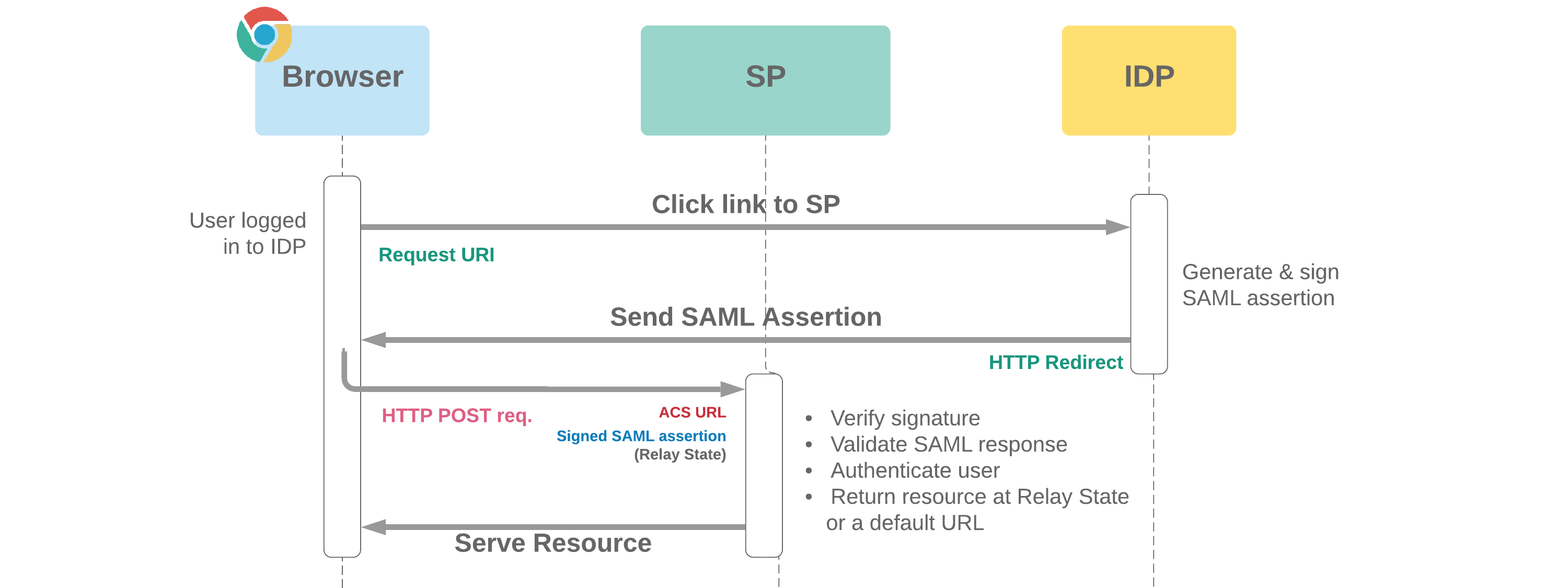
- Provides a method of using credentials for applications which don't offer SAML to login to Salesforce
- My domain is not required
- Delegated authentication SOAP endpoint must comply to specific WSDL (which can be downloaded from Salesforce)
- Password is not validated in SF and instead passed to authentication service for validation, so Salesforce password policy doesn't apply
- This flow requires delegated authentication endpoint to support processing passwords
- Delegated authentication can be enabled / disabled by an admin from Single Sign On Settings
- Permission "Is Single Sign-On Enabled" controls by user whether passwords are submitted to delegated authentication service
SAML migration trick: It can be useful to block certain users from logging in with username and password. By enabling delegated authentication and using the "Is Single Sign-On Enabled" permission, these users will be prevented from using their Salesforce password to login