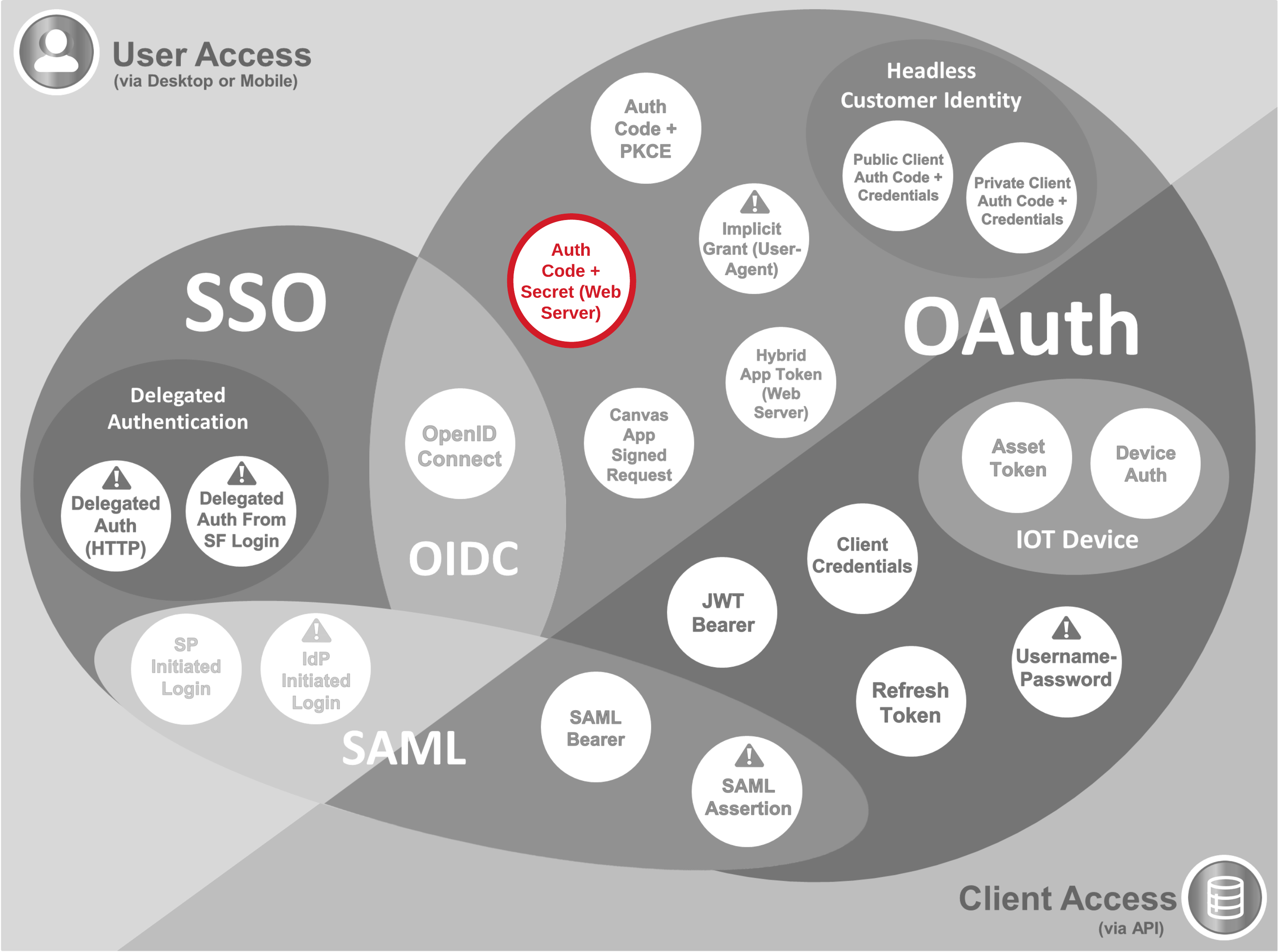
- This flow provides the highest level of security possible through standard OAuth flows, but is suitable only if the client secret can be protected by the client application - generally this is the case when the application has a back end server component which is operating in a trusted environment (e.g. an internal enterprise server application)
- The current IETF OAuth working group recommendation is for public and confidential clients participating in any auth. code flow to implement PKCE using code_challenge and code_verifier (more info on how these are used in the Authorisation Code with PKCE flow below)
- As an alternative to client secret, a JWT with issuer & subject = client_id signed with the client app's key can be provided in the access token request. For this variation, client_assertion and client_assertion_type should be set instead of client_secret
- The Salesforce "Web Server" flow is an implementation of this flow where Salesforce is acting as the authorisation and resource server
- Salesforce can also participate as the client in this flow
Documentation
Reference Implementations
This Flow in Context