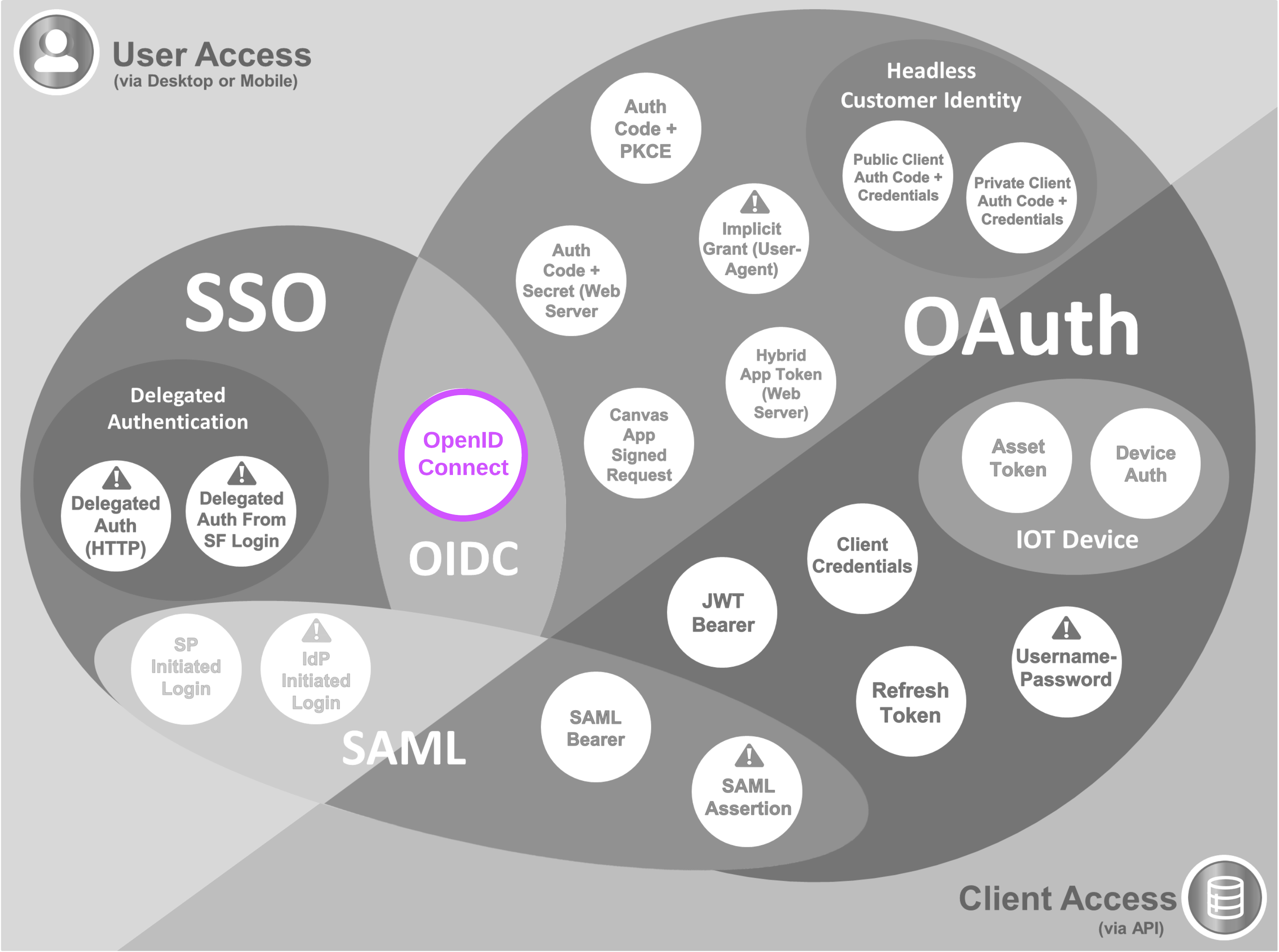
- OpenID Connect is the accepted standard and most popular mechanism for identity verification using the OAuth 2.0 framework. Salesforce allows OpenID Connect providers to be set up as authentication providers for Social Sign On with simple configuration
- Many identity services offer an identity verification mechanism based on OAuth 2.0 and similar to but not completely consistent with OpenID Connect. It's possible to set up custom authentication providers for services like these by extending the
Auth.AuthProviderPluginClassclass with custom logic to initiate authentication and retrieve user information (details in Salesforce documentation) - OpenID Connect is offered by services such as Google and Microsoft, and is likely used in the pre-configured authentication providers available for these services
- Some popular OAuth-based identity services which don't comply entirely with the OpenID Connect spec are also pre-configured in Salesforce. Examples include:
- Facebook (which offers Facebook Login)
- Twitter (Login with Twitter)
- LinkedIn (Member Authorization API and Profile API for user attributes)
- GitHub (Allows retrieving a user's profile info after securing an access token)
- A Salesforce org can also act as the OpenID Connect Provider for other applications. In this instance, either the web server version (as shown) or another OAuth flow could be used for the authentication/authorisation
- In addition to Social Sign On, authentication providers in Salesforce can be used to authenticate content providers for Salesforce Files Connect (e.g. Google or Office 365)
- Client id and secret are managed by Salesforce for standard authentication providers (Facebook, Google etc), though these can be overridden in the org if required
General details around characteristics of OpenID Connect:
- Nonce if provided is included as an attribute in the ID token - this binds the token to a specific authorisation request and help protect against replay attacks possible through CSRF
- The UserInfo endpoint can be used to provide ID claims not included in the scope of the ID token, for example picture, email, website, locale, phone number etc
- The draft OpenID Connect Session Management spec recommends the RP to regularly verify the session is still active at the OP, although these checks aren't made in the current Salesforce Auth. Provider implementation
- The OpenID Connect Core spec includes details on implementation of this flow
Documentation