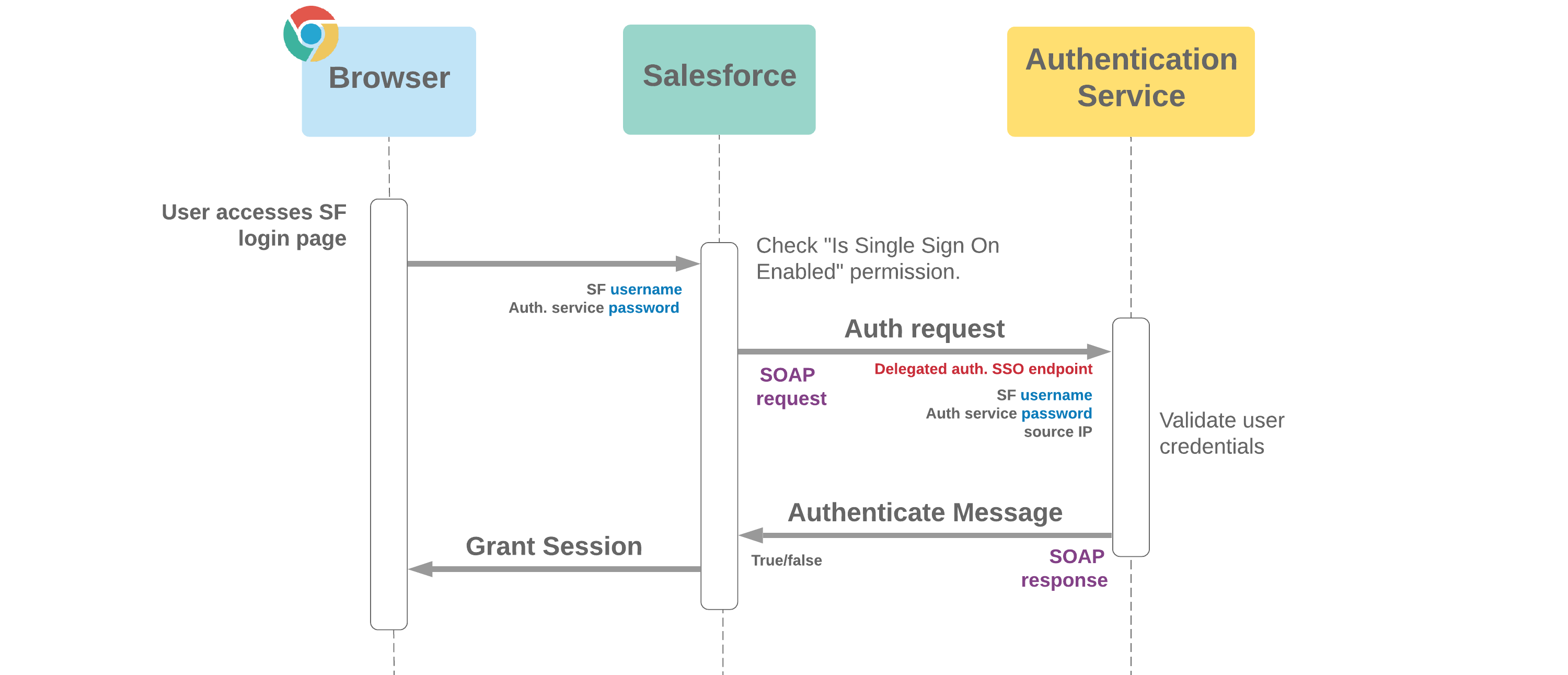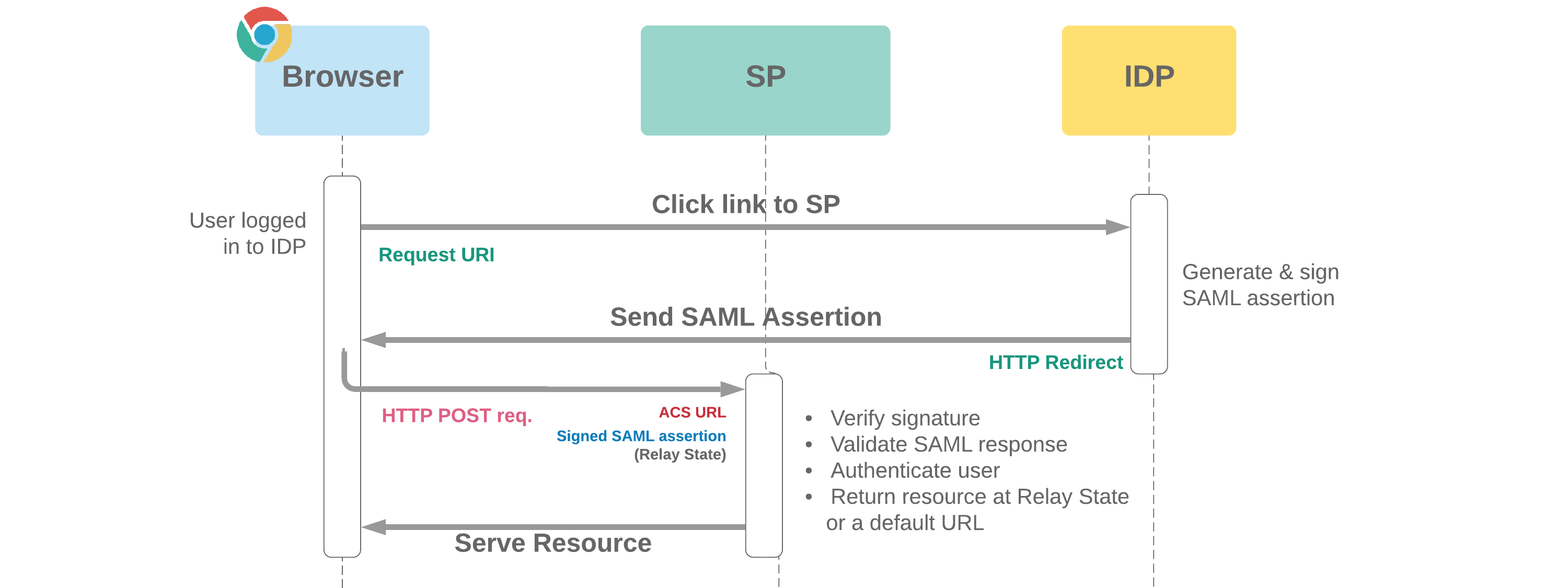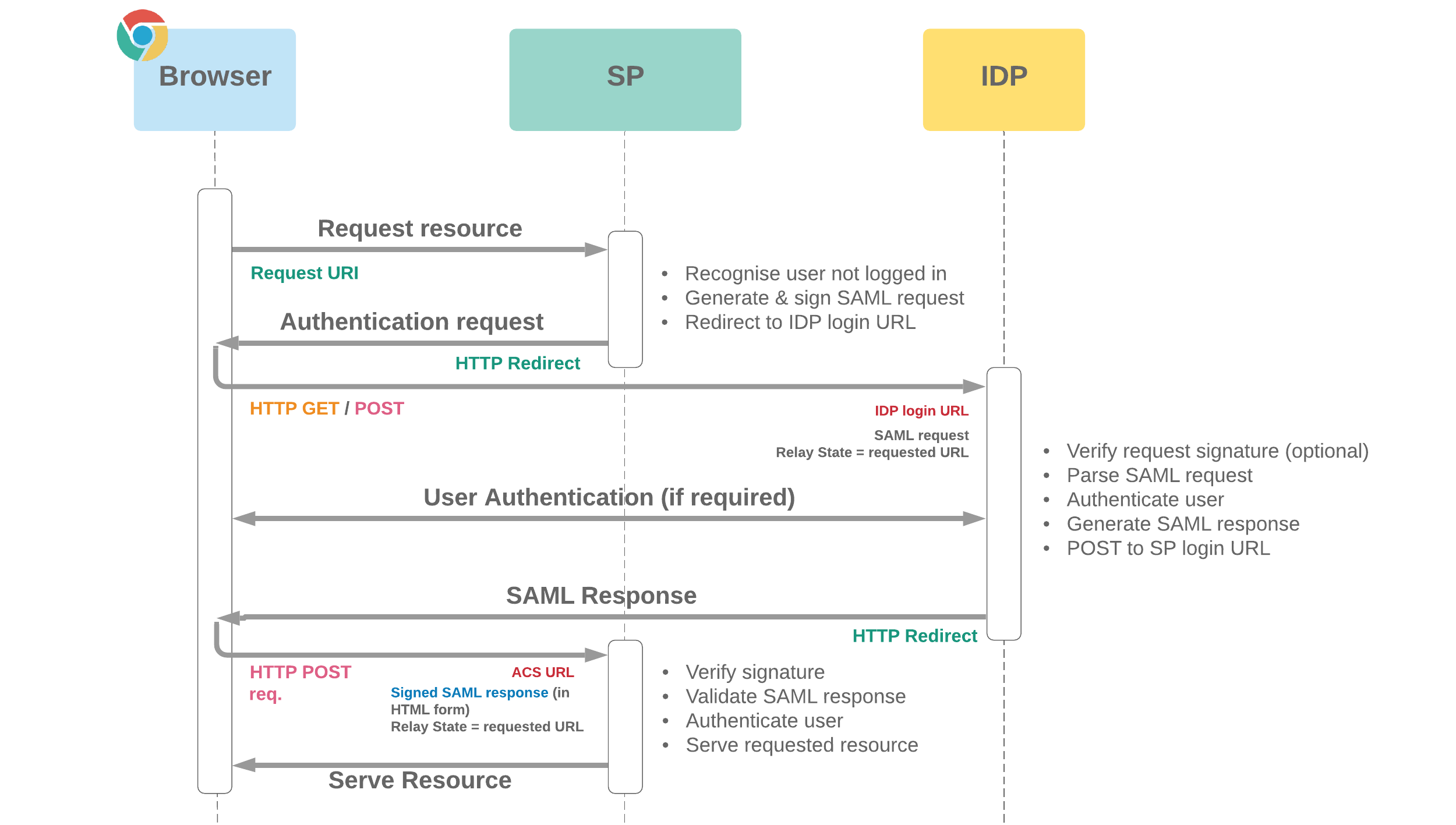
If Salesforce acts as the Service Provider:
- Salesforce "Single-Sign On Settings" should be configured with values from the IDP
- Certificate from the IDP should be uploaded as the identity provider certificate in Salesforce. This is used for signature validation on incoming SAML responses
- Requests will be signed by Salesforce with the selected certificate, which can be validated by the IDP if necessary
- IDP-encrypted assertions are also supported, and decryption certificate uploaded and selected as Assertion Decryption Certificate
- SAML request bindings can be configured to be bound to HTTP Redirect or HTTP POST (determines whether initial SAML authentication request is GET or POST)
- Just In Time (JIT) user provisioning can be configured to enable automatic creation/update of users based on contents of incoming SAML assertions. Salesforce will attempt to match a user and will either update this record or create a new user in real time. Standard provisioning allows assertion attributes corresponding to standard field names to be used for matching and values for field contents, or custom logic can be defined in a class implementing the
Auth.SamlJitHandler interface - The IDP will need to be set up with the Authorisation Consumer Service (ACS) URL ("Salesforce Login URL") and Entity ID
- MyDomain required for SP-Initiated SSO, which enables deep linking (landing on requested URL) and OAuth with SAML
For Salesforce to act as the Identity Provider:
- Salesforce identity provider setup must be enabled, and a connected app set up for each service provider specifying the Authorisation Consumer Service (ACS) URL and service provider's Entity ID, as well as general SAML configuration, which can differ by service provider
- User profiles or permission sets must be added to connected app for accounts to be used for SSO identity
- Optionally, SAML request signatures for a service provider can be validated by uploading the SP's signing certificate
- SAML responses can be encrypted for additional security
- The connected app's Start URL is used as Relay State if the app's icon is clicked in the Salesforce app launcher